Manage volumes and volume types¶
Volumes are the Block Storage devices that you attach to instances to enable persistent storage. Users can attach a volume to a running instance or detach a volume and attach it to another instance at any time. For information about using the dashboard to create and manage volumes as an end user, see the OpenStack End User Guide.
As an administrative user, you can manage volumes and volume types for users in various projects. You can create and delete volume types, and you can view and delete volumes. Note that a volume can be encrypted by using the steps outlined below.
Create a volume type¶
- Log in to the dashboard and select the admin project from the drop-down list.
- On the Admin tab, open the Volume tab.
- Click the Volume Types tab, and click Create Volume Type button. In the Create Volume Type window, enter a name for the volume type.
- Click Create Volume Type button to confirm your changes.
Note
A message indicates whether the action succeeded.
Create an encrypted volume type¶
Create a volume type using the steps above for Create a volume type.
Click Create Encryption in the Actions column of the newly created volume type.
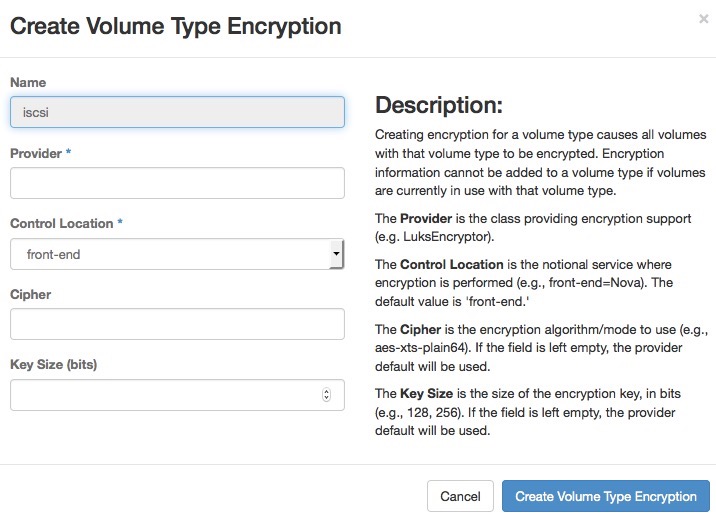
Configure the encrypted volume by setting the parameters below from available options (see table):
- Provider
Specifies the class responsible for configuring the encryption.
- Control Location
Specifies whether the encryption is from the front end (nova) or the back end (cinder).
- Cipher
Specifies the encryption algorithm.
- Key Size (bits)
Specifies the encryption key size.
Click Create Volume Type Encryption.
Encryption Options
The table below provides a few alternatives available for creating encrypted volumes.
| Encryption parameters | Parameter options | Comments |
|---|---|---|
| Provider | nova.volume.encryptors. luks.LuksEncryptor (Recommended) | Allows easier import and migration of imported encrypted volumes, and allows access key to be changed without re-encrypting the volume |
| nova.volume.encryptors. cryptsetup. CryptsetupEncryptor | Less disk overhead than LUKS | |
| Control Location | front-end (Recommended) | The encryption occurs within nova so that the data transmitted over the network is encrypted |
| back-end | This could be selected if a cinder plug-in supporting an encrypted back-end block storage device becomes available in the future. TLS or other network encryption would also be needed to protect data as it traverses the network | |
| Cipher | aes-xts-plain64 (Recommended) | See NIST reference below to see advantages* |
| aes-cbc-essiv | Note: On the command line, type ‘cryptsetup benchmark’ for additional options | |
| Key Size (bits) | 512 (Recommended for aes-xts-plain64. 256 should be used for aes-cbc-essiv) | Using this selection for aes-xts, the underlying key size would only be 256-bits* |
| 256 | Using this selection for aes-xts, the underlying key size would only be 128-bits* |
* Source NIST SP 800-38E
Note
To see further information and CLI instructions, see Create an encrypted volume type in the OpenStack Configuration Reference.
Delete volume types¶
When you delete a volume type, volumes of that type are not deleted.
- Log in to the dashboard and select the admin project from the drop-down list.
- On the Admin tab, open the Volume tab.
- Click the Volume Types tab, select the volume type or types that you want to delete.
- Click Delete Volume Types button.
- In the Confirm Delete Volume Types window, click the Delete Volume Types button to confirm the action.
Note
A message indicates whether the action succeeded.
Delete volumes¶
When you delete an instance, the data of its attached volumes is not destroyed.
- Log in to the dashboard and select the admin project from the drop-down list.
- On the Admin tab, open the Volume tab.
- Click the Volumes tab, Select the volume or volumes that you want to delete.
- Click Delete Volumes button.
- In the Confirm Delete Volumes window, click the Delete Volumes button to confirm the action.
Note
A message indicates whether the action succeeded.

Except where otherwise noted, this document is licensed under Creative Commons Attribution 3.0 License. See all OpenStack Legal Documents.